Google sponsored project Borg to the Cloud Native Computing Foundation (CNCF) in 2016. Consequently, Kubernetes became one of the most thriving open-source projects in the history of IT. After the usual movement through the hype cycle of Container Orchestration technologies, K8 is now mature and ready for enterprise grade production environments.
Moreover, many platforms like VMware with Tanzu, Red Hat and OpenShift or AKS by Azure, exist. These cloud providers offer their flavored K8s products, that fit into their ecosystem and heavily rely on automation and security.
Now, companies that adopted the K8s stack and started operating microservices arrive at new challenges. For example, managing multi tenancy and multiple cluster environments.
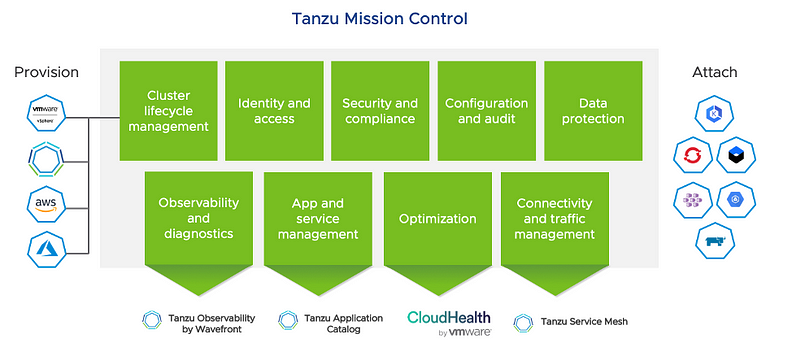
So, Tanzu Mission Control (TMC) is a relatively new product which offers diverse functions to supervise these environments in a single pane of glass. It reached General Availability on June 4, 2021. … and I already stressed that out, but more about hands-on soon.
Kubernetes — How It Works
Container Images are built via docker or any OCI compliant scheme. Kubernetes itself orchestrates the provisioning of containers with its components and offers massive functionality through vast integrations.
PODs, the smallest unit in K8s, regularly part of a deployment, contain one or more containers which start and stop together.
Master-Nodes handle the magic, and Worker-Nodes offer resources for diverse apps contained in namespaces, often as a deployment. Converged test environments with one consolidated Master/Worker Node are possible too.
Finally, to provide reliable services to customers outside the K8s cluster, you need to integrate a (cloud) load balancer. Subsequently, you can provision services Type Cluster-IP and Ingress Controller.
The performance benefit regarding bare metal K8s cluster vanish after considering scaleability. So, virtualized K8s clusters is mostly the way.
Overall, K8s uses the desired state principle. You typically describe this state in YAML files.

It associates with the military flavored OODA loop. But this is out of scope today as well.
What About The Integrations?
Many catalogs with building blocks, like official vSphere with Tanzu documentation, GIT repos and the CNCF projects, are reliable sources. These are, for example, Helm, Contour, Velero, Tanzu Extensions and an incredible amount more.
In addition, the deployment of a private Container Registry like Harbor is typically the first step after getting the K8s stack up and running. You store the container images and other objects in a registry, which your K8s cluster uses to retrieve container images from. Basically, after an established trust. (Certificates/Secrets)
Adapt the Lego mindset because Kubernetes and Containers are as modular as building blocks. Finally, don’t forget to bring your growth mindset, failure is an opportunity to grow. In the end, a painful and exciting cloud native journey awaits you.
What About Tanzu?
The VMware Tanzu Suite makes Kubernetes Cluster Deployments “Boring” (Tanzu for Kubernetes Operations — TKO). Tanzu Kubernetes Grid (TKG) is a flavored product with multiple extensions like TAP, TAC and TAS. It orchestrates not container but Tanzu Kubernetes Cluster itself and other services. The prime goal is that developers can focus on building that code.

To understand the TKG terminology better, I refer to the veducate Blog article.
These presently TKGs, TKGi and TKGm editions have very diverse architectures and a lot of modularity, especially TKGs with vDS and NSX-T. There will be considerable changes in the near future. (TKG 2.0)
Tanzu Community Edition for free.
Personally, I made numerous experiences with the vSphere with Tanzu stack (TKGs). TKGs and the Supervisor Cluster for lifecycle Management gets the vSphere Admin excited.

Of course, the complexity depending on Cluster API and K8s itself makes it hard to learn. But it is relatively convenient if you are already experienced with vSphere, vSAN and Networking. Essential book tip, thanks Cormac Hogan: kubernetes-for-vsphere-administrators
With TMC, you have a GUI besides the vCenter/CLI only, that makes life easier as an vSphere Admin as well.
Tanzu with TMC integrates well into vCenter, vSAN, NSX-T, NSX Advanced Load Balancer, vRealize Automation, Operations, vCloud Director and many other VMware products.

You can easily deploy and govern multi cluster environments and manage them with TMC (included in Tanzu Standard Add-On for vSphere).
Tanzu takes care of the K8s stack and base image provisioning and much more.
Multi-Cluster Management: Access TMC
Not just Multi-Cluster, but also Multi-Cloud. Attach different cloud environments and use backup / DR targets. There are sometimes requirements that data is kept On-prem, this is possible with local S3 targets like Netapp Storage Grid or open source MinIO.
I will refer to vSphere with Tanzu (Private Cloud) and Azure AKS (Public Cloud) for examples.
Therefore, TMC itself, is only available as a SaaS Instance on AWS. When Frankfurt finally arrives to select? It is quite foggy :-).
Nevertheless, TMC is a very tangible K8s cloud management plane.

Agents in the Kubernetes management or workload cluster pull the configuration from the cloud plane *tmc.cloud.vmware.com via outbound, no inbound connections. As easy as that.
After you selected the organization with the super admin rights, you can assign roles via https://console.cloud.vmware.com


Setup complete! Let’s have a look at the cloud plane:

In the VMware cloud console, you have additional security and access related possibilities. Like Active Directory integration or Two-Factor Authentication.
Another possibility is to generate an access token and connect via Tanzu CLI or API.
Features Overview
Lifecycle and Configuration Management
Manage/Attach different clouds like Azure with AKS and subsequent clusters. Create, Update, Delete K8s cluster with great visibility.


Furthermore, you can easily scale or replace the individual K8s nodes. More and more AI accelerators are integrated, like Nvidia GPUs for a “GPU-Node-Class” in vSphere with Tanzu.

Compliance / Policy Engine
Many types of adjustable policies like network policies can be attached to clusters (groups) and namespaces. As always, it depends.
Data Protection
Velero is the open-source standard for backups in TMC. It is included in the subscription. TMC manages and configures the Velero agents.
A compatible S3 Object Storage, providing backup / disaster recovery target buckets, is mandatory for the Velero (+Restic). Other companies like Veeam with Kasten allow for NFS usage to backup your cluster objects and persistent volumes.
You can one-click install Velero with TMC and start scheduling backups in the Cluster overview by “Enable Data Protection”. Be aware that you need a compatible S3 target / bucket and also a valid configuration. These S3 targets are centrally managed in TMC administration plane. Certificate Management is important and tricky in this case as well, some features are missing in the GUI.

Licensing
Available as one or three-year subscription (SaaS).
TMC is included in vSphere with Tanzu Standard and in new vSphere + Edition. Or you directly license your K8s cores for TMC.

Register a Tanzu Management Cluster


For example, a vSphere with Tanzu Supervisor Cluster (HA+DRS) built upon ESXi Enterprise Plus Nodes. In this case, the Supervisor Cluster is the Management cluster.
Roadmap
Tanzu Mission Control Starter Edition has been announced, but I think it’s not widely available.
Furthermore, several new features, like restoring with Velero to another K8s Clusters by the GUI, will be released soon.
I will follow up with hands on and more in depth configuration in the next article.
So stay tuned… and thanks for reading.


